Do you believe that a DKIM signature and an SPF record are enough to protect your email from spooking? Do you want to add another email deliverability practice that would make your email outreach safer and a bit more informative? Do you want to have more control over your outreach?
Then you need a DMARC record. A relatively new addition (albeit, not so new compared to BIMI), a DMARC record allows you to write your own policy regarding the processing of your emails by the receiving side and contribute to making email marketing a safer practice.
What is a DMARC record?
It’s a TXT record for your domain name system. Standing short for Domain-based Message Authentication, Reporting, and Conformance, DMARC serves as an anti-spoofing and anti-phishing measure.
- It doesn’t let spammers exploit your domain name. Spammers can worm their way past many defenses. They can forge “From” headers, send fake emails using the domain name of a company that has authority in your industry or even affect your lifestyle. For example, many spoofers sent emails from FDA and WHO during the COVID-19 pandemic in order to steal account information, plant malware or ransomware.
- It keeps your inbound outreach safe. Some spoofers would go and try to compromise your entire network by sending a fraudulent email from a “colleague”. Anyone who opens that message may end up clicking a link or downloading harmful software. However, with a DMARC record in place such emails get intercepted and quarantined.
DMARC is impossible without implementing two other anti-spoofing measures such as SPF and DKIM.

With SPF and DKIM in place, it’s up to internet service providers to decide whether they should reject incoming messages, quarantine them or let them pass. But adding DMARC to the mix provides you with the benefits that are hard to ignore:
- Transparency. Whenever a suspicious incoming message arrives, DMARC sends you a report that specifies why this email was considered suspicious and mentions the authentication checks it failed. Therefore, you’re able to see whether you’re targeted by spoofers or getting contacted by a sender who has DNS settings issues.
- Reputation safety. Since DMARC makes sure that no spoofed email would reach your inbox, you don’t have to worry about getting malicious content or downloading ransomware and endangering your employees and your clients. You’re also guaranteed to get fewer spam complaints or get reported by internet service providers because of some mishap (marketing emails still coming to an abandoned employee inbox, etc.) preventing spoofed emails from reaching users can lower spam complaints and protect your domain‘s reputation with internet service providers.

Why do you need DMARC reports?
With DMARC reports, you can learn the following:
- What servers or third-party domains send emails on your behalf
- How many messages pass DMARC check successfully
- What servers, apps or services send emails that fail authentication checks
- What DMARC policy the recipient server uses when receiving emails that failed authentication check
To sum it up, with DMARC reports, you’re well aware of your domain’s sending activity. Therefore, you can pinpoint your problematic servers and services, fix issues that cause deliverability problems and make sure that all domains that send on your behalf have an SPF record and a DKIM signature.
Setting up DMARC
One of the most common myths related to a DMARC is that it’s very easy to set up. What can be so hard about adding a simple TXT record?
This way of thinking usually leads to DNS issues and low domain reputation. Changing any DNS record takes knowledge and time, not to mention that there is a considerable waiting period involved. So our first advice regarding DMARC setup is to do it with professional help. Our second advice is to build a step-by-step plan.
1. Add a DMARC record
To get started, you need to access the dashboard on your hosting website. Dig into the Settings and find DNS record management. Next, you need to create a TXT record.
A DMARC TXT record consists of multiple tags. Some of them must be featured in your record regardless of your intention, some of the help to inject more flexibility into your sending activity management.
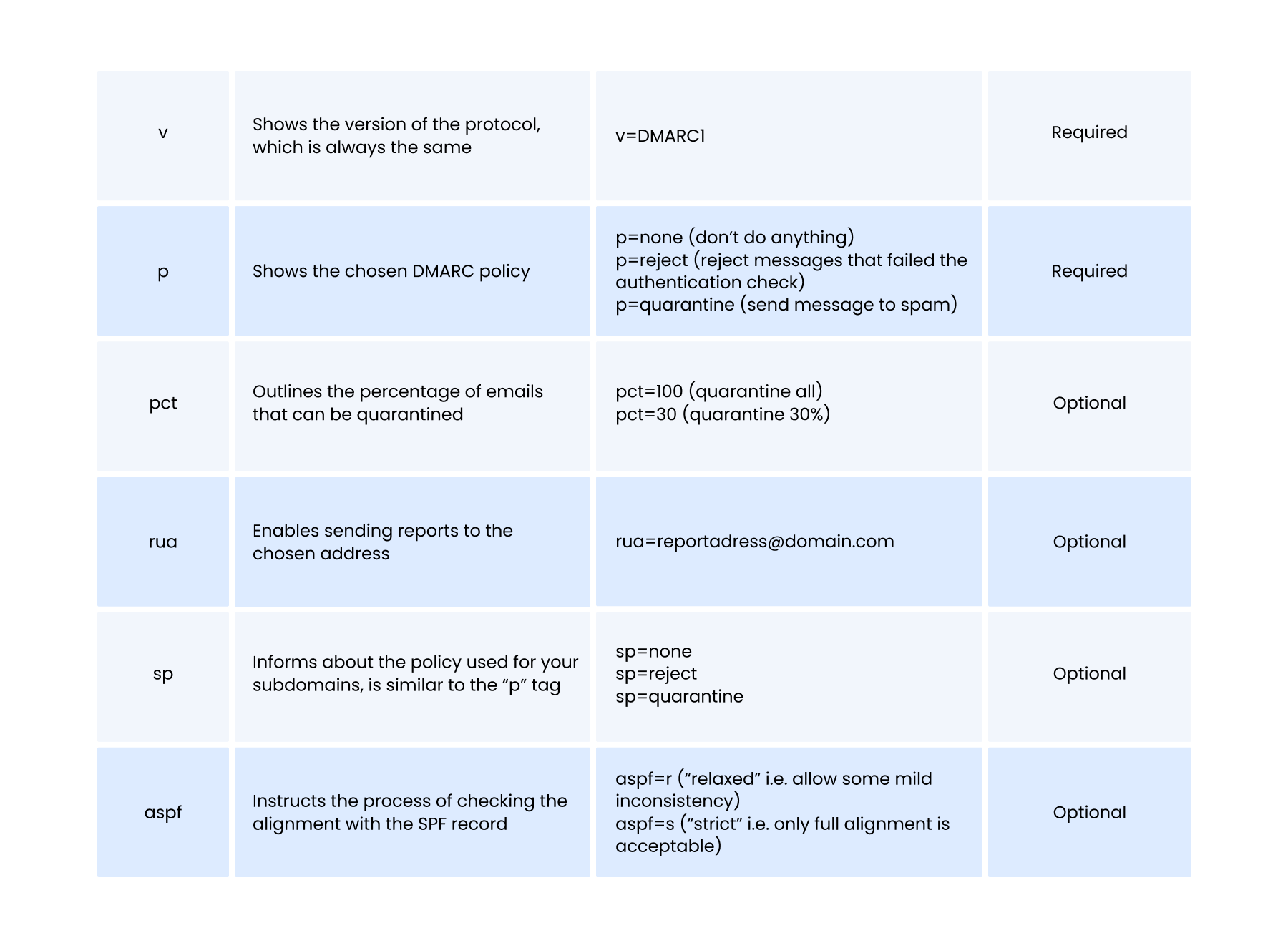
Based on these tags, we can rule out five types of DMARC records, most commonly used by email senders.

After you add the record, save changes and wait for your hosting website to implement them.
2. Deploy your DMARC record
It’s not enough to create and set up a DMARC record. You must make sure that it fits your sending activity like a glove. Figuring it out is the hardest part of the DMARC policy set up.
First things first, choose a “p=none” policy for your DMARC record even if you send emails in bulk.
V=DMARC1; p=none; rua=dmarcreport@domain.com
Trust us, by using policies like “p=reject” or “p=quarantine” without knowing all your sources, will end with you sentencing some of your top-notch cold email templates to spam folders.
Gather all sources
Before you know which policy regarding incoming emails you should accept, you must know everything about your incoming emails. Do you know all services (support, email deliverability tools, email marketing providers, administrative tools) that send email to you?
If your answer is “yes”, then you either have an amazing memory or are too shy to admit that you don’t know everything. Don’t worry, almost everybody doesn’t know all the sources. After all, we all are busy handling billions of daily tasks.
Moreover, you don’t have to memorize everything, not with DMARC reporting. This built-in feature allows you to get insights about your email traffic and take note of all messages that pass or fail the check.
The reason why we suggest using “p=none” is that it creates a testing mode for your DMARC, so internet service providers would take notice of every incoming email, but wouldn’t take action. Instead, you will receive reports about incoming messages. Within this mode, you’ll quickly gather information about your email traffic and learn all about all your sources.
But that’s not all.
At that point, you’re dealing with a tremendous amount of reports. Each of these reports looks like that:

If you feel intimidated by this report’s volume, it’s possible to convert it into something that pleases the eye and doesn’t activate your panic mode. For example, GlockApps has the DMARC Inspector tool that turns those freaky XML files into neat tables:

Here comes the most tedious part: separating legitimate sources from non-legitimate ones. You want to be sure that all domains and IP addresses you send from are featured in your SPF record and have the DKIM signature. To make it easier for you, you can do the following:
- Write down all the sources you send emails to and from
- Write down all the sources that send emails to you
Now, whenever you encounter new sources in a report, try to find a match in your list. They are usually connected with the sources you use (support tools, apps, etc). You’re also guaranteed to come across domains or IP addresses that you won’t be able to identify in any way. However, if there are a few of them, you can proceed with choosing policies. You don’t need your SPF and DKIM to cover all sources, just the ones that matter to your email marketing.
Keep monitoring
As you continue to watch your reports and get confident about your results, you can move on to the next deployment phase, which consists of accessing your DNS records and changing your “p=none” policy to “p=quarantine”. Start with quarantining 1% of messages (add pct=1). Then, after a week of monitoring, change “pct=1” to “pct=5”, letting the receiving servers filter 5% of messages that fail authentication check. In a week, make it 10%. Then 25%. Then 50%. Then 100%.
The increase of emails to be quarantined for failing to pass the authentication check should match the increase of your confidence about your deliverability. If your reports show that your sources align with their DKIM and SPF, no email sent from your behalf and from a source that you know, would fail the check.
Conclusion
Like all other important DNS records, DMARC is a tricky one. It won’t do you any good without a DKIM signature and an SPF record, but once you got it covered, it will make sure that you would always know when any message sent by you fails to comply with the SPF guidelines or has issues with a DKIM key. In case you found yourself overwhelmed by the complexity that is DMARC record deployment, worry not. Our experts are ready to help you out with advice or a consultation. Let us know if you’d like to connect!